What Are The Benefits Of Risk Management Policies?
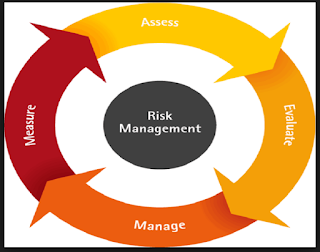
Risk Management Policies is the manner of identifying, assessing and controlling threats to an organization's capital and earnings. These risks stem from a range of sources including monetary uncertainties, legal liabilities, technological know-how issues, strategic Management errors, accidents and natural disasters. A profitable Risk Management program helps an employer consider the full vary of risks it faces. Risk Management also examines the relationship between risks and the cascading effect on they could have on an organization's strategic goals. Risk Management Policies This holistic strategy to managing Risk is sometimes described as company Risk Management because of its emphasis on watching for and understanding Risk throughout an organization. In addition to a focus on inner and external threats, organization Risk Management (ERM) emphasizes the importance of managing advantageous risk. Positive risks are possibilities that could make a bigger business price or,



