Future-Proofing Your Business: Adapting IT Security Policies to Emerging Threats

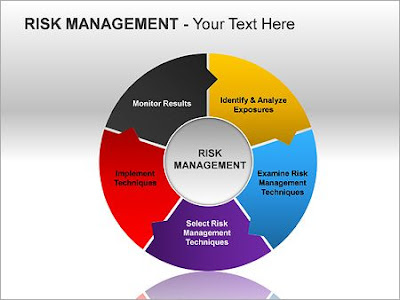
In today's digitally driven landscape, small businesses are increasingly becoming targets for cyber threats. Despite their size, these enterprises possess valuable data that is attractive to cybercriminals. As a result, having robust information security policies in place is paramount to safeguarding sensitive information and maintaining the trust of customers and stakeholders. Information security policies, often referred to as I T security policies , serve as the foundation for protecting data assets and mitigating risks within an organization. For small businesses, these policies are not only essential but can also be a competitive advantage in a crowded marketplace. IT security policies One of the primary objectives of an information security policy for small businesses is to establish guidelines and procedures for safeguarding data from unauthorized access, disclosure, alteration, or destruction. This includes implementing measures such as encryption, access controls, and...
.jpg)