Enhancing Your Security Policy Templates with Top Cyber Security Policies

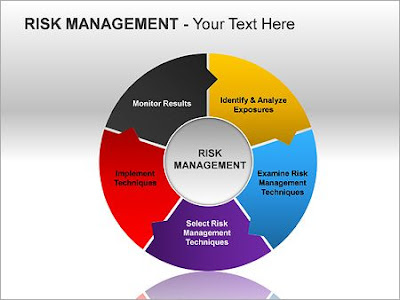
In today's digital age, cyber security is a top priority for businesses of all sizes. Robust cyber security policies are essential for protecting sensitive data, ensuring compliance with regulations, and maintaining customer trust. One of the most effective ways to develop and maintain these policies is through the use of security policy templates. These templates provide a structured framework that helps organizations create comprehensive and effective cyber security policies. Why Cyber Security Policies Matter Cyber security policies are formal documents that outline an organization's strategy for protecting its information systems from cyber threats. These policies cover a wide range of areas, including data protection, access control, incident response, and network security. By clearly defining roles, responsibilities, and procedures, cyber security policies help organizations mitigate risks and respond effectively to security incidents. Cyber security policies The Ro...