Major components of Risk management policies
Every company faces risks, some of which
are consciously selected and others which are a natural part of the surroundings
in which the company operates. Establishing a company, putting items on the
market, hiring staff, gathering data, and developing processes are all crucial
steps in expanding a successful firm. Additionally, each of them poses a danger
anf require Risk Management Policies.
 |
| Risk Management Policies |
However, if a company doesn't strike a
healthy balance between taking risks and minimising them, it won't last very
long. That is what risk management is about. Read the blog to know major
components of Compliance Policies
and risk management policies.
What
Elements Make Up Risk Management?
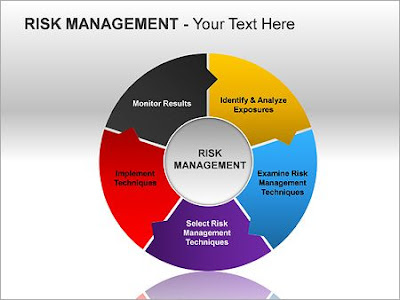
There are many ways to group the essential
parts of an efficient risk management process, but it must at the very least
include the risk management aspects listed below.
Identification
of Risk
The process of identifying prospective
hazards and then classifying the actual dangers the company encounters is known
as risk identification. The term "risk universe" can refer to the
entire set of prospective and existing dangers. There is less chance that
prospective sources of risk will be overlooked when all potential hazards are
methodically identified.
 |
| Compliance Policies |
Risk
Evaluation
Analysing risks' likelihood and possible
effects comes next after they have been discovered. What may a risk's potential
costs be if it materialises? According their potential to cause disruption,
risks may be classified as "high, medium, or low" or "serious,
moderate, or minor" by an organisation.
The technique of classification itself is
less significant than the understanding that certain hazards provide a more
urgent threat than others. Businesses use risk analysis to prioritise
mitigation.
Response
Preparation
Planning the responses provides an answer
to the question: What will you do about it? For instance, your response
strategy can include safety education if you discovered during detection and
evaluation that the company is vulnerable to phishing assaults because its
personnel are uninformed about email security best practises.
Conclusion
It's critical to realise that managing risks
is a continuous activity that occurs over the course of an organization's
existence as it works to foresee hazards and proactively address them earlier
they have a negative impact.



Comments
Post a Comment