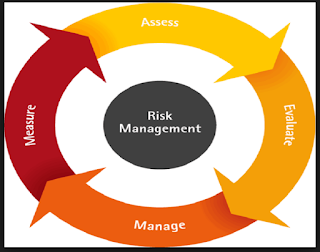
Major components of Risk management policies
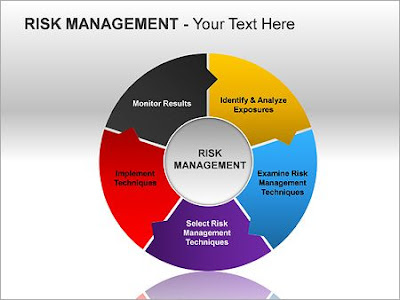
Every company faces risks, some of which are consciously selected and others which are a natural part of the surroundings in which the company operates. Establishing a company, putting items on the market, hiring staff, gathering data, and developing processes are all crucial steps in expanding a successful firm. Additionally, each of them poses a danger anf require Risk Management Policies . Risk Management Policies However, if a company doesn't strike a healthy balance between taking risks and minimising them, it won't last very long. That is what risk management is about. Read the blog to know major components of Compliance Policies and risk management policies. What Elements Make Up Risk Management? There are many ways to group the essential parts of an efficient risk management process, but it must at the very least include the risk management aspects listed below. Identification of Risk The process of identifying prospective hazards and then classifying the actua...